In recent years, the energy sector in the US has been facing a greater threat from cyberattacks. It is particularly vulnerable considering the increasing grid modernisation and digitalisation of utilities. In view of this, the federal government is undertaking a detailed assessment and making calculated efforts to mitigate cyber risks through various action plans.
In the latest move, on September 26, 2019, US Senator Lisa Murkowski and four other colleagues introduced a bill titled “Protecting Resources on the Electric Grid with Cybersecurity Technology Act or PROTECT Act of 2019” in the Senate. The bill proposes to effectively safeguard the national power grid from global cybersecurity threats. “The threat of cyberattacks by our foreign adversaries and other entities is real and growing. This bill works to ensure utilities can invest in advanced, cutting-edge cybersecurity technologies,” says Murkowski. Given the bipartisan support for the bill, it is expected to pass through the Congress and result in several benefits to the country’s electricity industry.
Earlier in the month, a new federal report by the US Government Accountability Office (GAO) outlined cybersecurity risks facing the US power grid and recommended measures that federal regulators and the US Department of Energy (DoE) can adopt to bolster grid security. Requested by the US House of Representatives’ Energy and Commerce Committee in 2015, the GAO study is part of a larger and ongoing examination of the power grid’s cyber defence system. Power Line presents the key highlights and of the recent developments in the US energy sector’s cybersecurity space…
Draft PROTECT Act, 2019
The bill proposes to amend the Federal Power Act to provide energy cybersecurity investment incentives and establish a grant and technical assistance programme for advanced cybersecurity technology investments at the DoE.
It directs the Federal Energy Regulatory Commission (FERC) to study how to encourage public utility investment in advanced cybersecurity technology and utilities’ participation in cybersecurity threat information sharing programmes. The FERC would then issue a rule to implement new incentive rate treatments to carry out those objectives within a year of the study’s completion.
The FERC would permit public utilities to apply for recovering the costs and incentives associated with qualifying cybersecurity investments over the depreciable life of assets on a single-issue basis. This implies that other aspects of the utilities’ rates would not be considered in any such proceedings; thereby enabling utilities to recover costs and obtain incentives without the risk of inviting litigation on all other aspects of their FERC-approved rates. FERC would have 180 days to study the issue, followed by another year from the study’s completion to issue a new rule adopting the incentive rate treatment.
The bill also calls for a grant and technical assistance programme, administered by the DoE, to encourage similar investments among non-jurisdictional utilities such as rural electric cooperatives and municipal utilities. The bill proposes funding of $50 million annually under the programme, during the period between 2020 and 2024.
The grants and technical assistance under the programme will be awarded to eligible entities on a competitive basis. The DoE is to develop the criteria and formula for the same. Priority will be given to eligible entities that have limited cybersecurity resources, own assets critical to the reliability of the bulk power system, as well as defence-critical electric infrastructure.
The energy secretary must, in consultation with FERC, North American Electric Reliability Corporation (NERC) and the Electricity Subsector Coordinating Council, establish this programme (Rural and Municipal Utility Advanced Cybersecurity Grant and Technical Assistance Program) within 180 days of the enactment of the Act.
 GAO report highlights
GAO report highlights
The GAO’s report includes highlighting of cybersecurity risks from internet-connected smart devices and coordinated cyberattacks across geographically dispersed areas. It found out that foreign nationals, criminal groups, terrorists and others are becoming increasingly capable of attacking the power grid through industrial control systems that support grid operations. The GAO also pointed out that the grid is becoming increasingly vulnerable with widespread adoption of high-wattage consumer internet of things (IoT) devices — or internet-connected smart appliances such as meters, thermostats and electric vehicles — and the use of global positioning systems for synchronising grid operations.
As per the report, smart devices allow the power sector to remotely monitor and reconfigure grid-supporting networks, but they also create vulnerabilities for their “increasingly-interconnected” business and industrial control systems. A cyberattack on transformers or other critical components could cause widespread and long-lasting power outages and could keep first responders away from accessing the necessary power supplies indefinitely. So far, although cybersecurity incidents have reportedly not resulted in power outages domestically, cyberattacks on industrial control systems have disrupted foreign electric grid operations. Further, the scale of power outages that may result from a cyberattack is uncertain due to limitations in recent federal assessments.
 Federal actions for CIP: The DoE, the Department of Homeland Security (DHS) and other federal agencies have performed various critical infrastructure protection (CIP) activities. They assist the grid asset owners and operators in implementing protection measures that mitigate cybersecurity risks, by providing capabilities to prevent cybersecurity intrusions and offering training and guidance on cybersecurity practices. Further, the DHS has taken initial steps to help grid entities in the management of supply chain cybersecurity risks.
Federal actions for CIP: The DoE, the Department of Homeland Security (DHS) and other federal agencies have performed various critical infrastructure protection (CIP) activities. They assist the grid asset owners and operators in implementing protection measures that mitigate cybersecurity risks, by providing capabilities to prevent cybersecurity intrusions and offering training and guidance on cybersecurity practices. Further, the DHS has taken initial steps to help grid entities in the management of supply chain cybersecurity risks.
Federal agencies also help grid entities in identifying cybersecurity risks and detecting incidents by providing threat and vulnerability information, performing risk assessments and conducting forensic analysis and research. For instance, the DoE piloted and launched the Cybersecurity Risk Information Sharing Program to provide a voluntary, bi-directional public-private IT data sharing and analysis platform.
The DHS’s automated indicator sharing programme provides a server housed at each participant’s location, which can be used to exchange threat indicators with the department’s National Cybersecurity and Communications Integration Center. The DoE’s Cybersecurity for Energy Delivery Systems programme sponsors grid cybersecurity research through its national laboratories.
Federal agencies have developed policies, strategies and plans to define their roles and responsibilities both for responding to, and recovering from grid cybersecurity incidents. The DHS has the responsibility of leading the federal effort to mitigate the impact of such incidents. The DoE coordinates the energy sector’s specific response with DHS and the Department of Justice. In a bid to promote state and local preparedness and resilience for future energy emergencies arising due to a cyber incident, the DoE, along with the National Association of State Energy Officials, has conducted regional energy assurance exercises.
FERC has performed a variety of regulatory activities aimed at addressing grid cybersecurity risks such as the following:
- Approve mandatory cybersecurity standards for bulk power system: In order to augment the existing standards (first introduced in 2009), FERC approved a new standard in October 2018, to strengthen the supply chain risk management protection for the US bulk electric system.
- Enforce regulatory requirements through imposition of civil penalties: Such a notification was issued in January 2019 when NERC assessed a $10 million penalty based on 127 violations of cybersecurity standards by an undisclosed entity.
- Audit the performance of the electric reliability organisation (NERC) and its regional entities: FERC monitors the level of resources that NERC devotes to cybersecurity oversight through its annual review of NERC’s budget.
- Audit bulk power entities for compliance with mandatory cybersecurity standards: Between 2016 and 2018, FERC conducted independent audits of eight bulk power entities for compliance with those standards and released reports on public lessons learned, based on the results. From 2019 onwards, FERC plans to conduct four such audits annually.
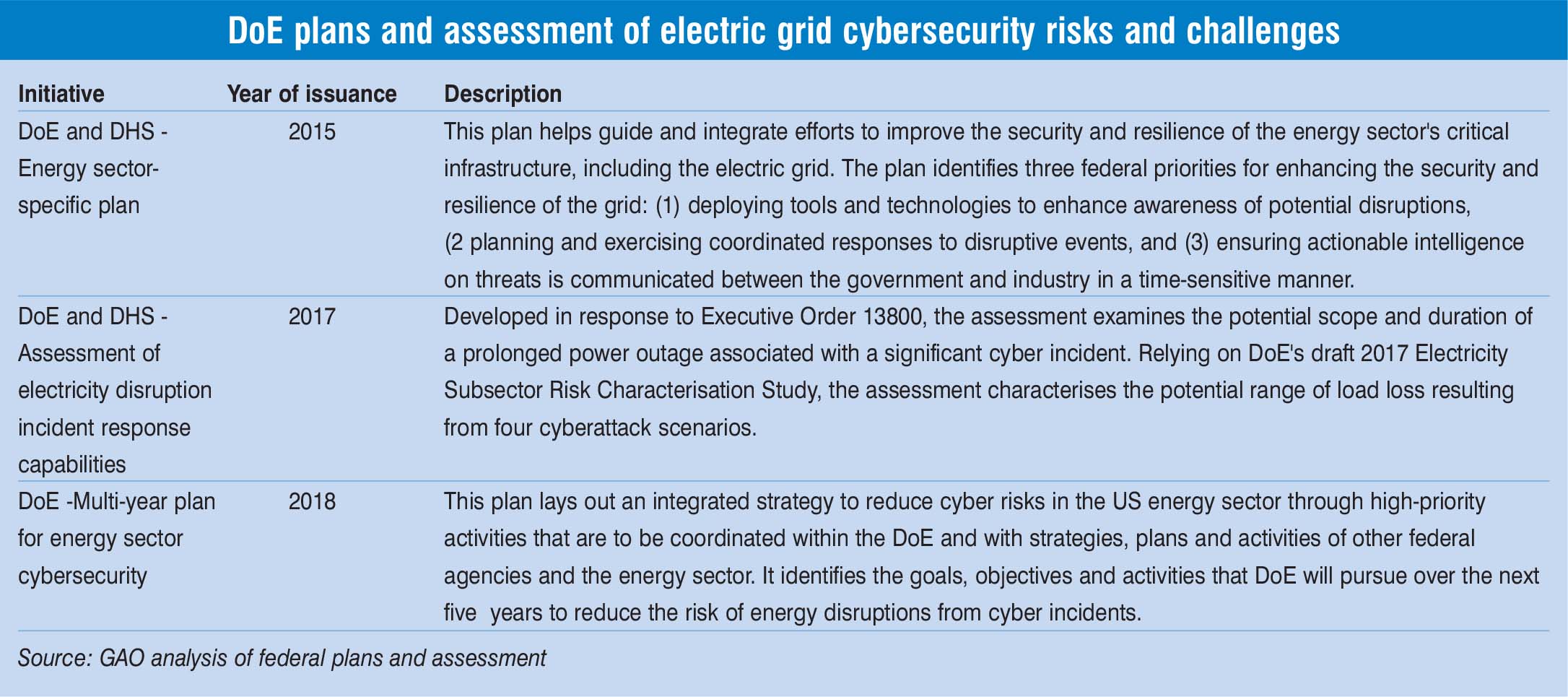 The GAO report points out that there is a need for DoE to have a complete grid cybersecurity plan to be able to provide proper guidance to decision-makers in allocating resources to address such risks. Further, FERC-approved mandatory grid cybersecurity standards do not necessarily address the leading federal guidance for critical infrastructure cybersecurity – particularly the National Institute of Standards and Technology (NIST) Cybersecurity Framework. It also points out that the FERC’s approved threshold, for which entities must comply with the requirements of the full set of grid cybersecurity standards, is based on an analysis that did not evaluate the potential risk of a coordinated cyberattack on geographically distributed targets.
The GAO report points out that there is a need for DoE to have a complete grid cybersecurity plan to be able to provide proper guidance to decision-makers in allocating resources to address such risks. Further, FERC-approved mandatory grid cybersecurity standards do not necessarily address the leading federal guidance for critical infrastructure cybersecurity – particularly the National Institute of Standards and Technology (NIST) Cybersecurity Framework. It also points out that the FERC’s approved threshold, for which entities must comply with the requirements of the full set of grid cybersecurity standards, is based on an analysis that did not evaluate the potential risk of a coordinated cyberattack on geographically distributed targets.
Based on its findings, the GAO report made the following recommendations to DoE and FERC:
- DoE, in coordination with DHS and others, should develop a plan to implement a federal cybersecurity strategy for the electric grid. It must ensure that the plan addresses the key characteristics of a national strategy, including a full assessment of cybersecurity risks to the grid.
- FERC should consider directing NERC to adopt any changes to the mandatory cybersecurity standards to better reflect the growing risks and ensure that those standards fully address the NIST Cybersecurity Framework.
- FERC should evaluate the potential risk of a coordinated cyberattack on geographically distributed targets. Based on the evaluation, it should determine whether to direct NERC to make any changes to the threshold for mandatory compliance with requirements in the full set of cybersecurity standards.
The latest developments augur well for strengthening of the cybersecurity strategy and implementation in the electricity bulk power system. This requires greater resources and manpower dedicated to the purpose. Further, the roll-out of new policies as proposed by the new bill will take time. After the enactment of the bill, FERC would have 180 days to study the issue and another year from its completion to issue a new rule adopting the incentive rate treatment. Utilities would then have to file individual applications with FERC seeking the desired incentive rate treatment.
The DoE would have to take a holistic view of developing a national cybersecurity strategy for the electric grid. The proposed grant programme by legislation would also encourage investments in advanced cybersecurity technologies among non-jurisdictional utilities. Net net, greater federal action is likely to take place to ensure strengthening of cybersecurity of the US electric grids in the coming months.
